We previously shared this post about the wrong way of protecting patient privacy where we were sent an encrypted file together with the password.
In contrast to this previous failure, we recently received another DVD a couple days ago, again with an encrypted file, but this time, with instructions to contact the medical office directly by phone to obtain the password. Presumably they will verify our identity and authorization before providing us the password to the file.
Since it's the weekend and their office is closed, it occurred to us that we could try breaking the encryption on the file, instead of waiting until next Tuesday to get the password.
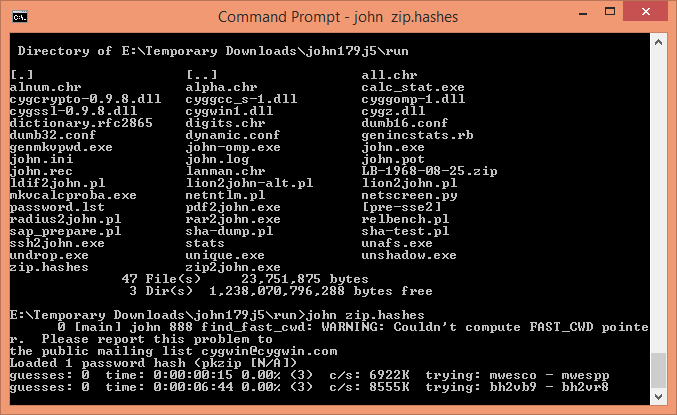
We therefore downloaded John the Ripper, an open source password cracker, followed these instructions, and set a modern desktop (a quad-core i7 with 16GB ram) to work.
The consequence? 0.01% of all possible passwords were tested in 24 hours, meaning it would take 100 days to test 1% of all possible passwords, 1000 days to test 10% of all possible passwords, or 10000 days to test all possible passwords.
While in theory we could speed up the process by using faster or more computers (e.g. by spinning up a large number of cloud-based servers), we'll just call the medical office on Tuesday to get the password instead of leaving our computer to guess passwords for the next 15 years.
The takeaway? Encryption, while not absolutely fool-proof, is an important tool to protect patient privacy. It just needs to be used correctly(*).
* For the cryptography experts out there, yes, we do know that there are better methods of key exchange than having us call our counter-party medical office for the secret key. Public-key cryptography is the better answer, without a doubt. Perhaps we'll start including our public key in our requests for patient health information and see how long it takes before another medical office actually uses it to encrypt the information. ;)